NPM Supply Chain Attack September 2025: 18+ Core Libraries Hit
Key Takeaways
- A renowned developer’s NPM account was compromised, affecting dozens of packages downloaded over 2 billion times weekly
- Malicious code operates as a “clipboard hijacker” – replacing cryptocurrency wallet addresses to steal assets
- The attack targeted foundational JavaScript libraries, potentially spreading across the entire Web3 ecosystem
- Hardware wallet users are safer due to their ability to verify each transaction before signing
- Major projects like MetaMask and Phantom have confirmed they were not affected
The NPM supply chain attacks have evolved from rare disruptions into one of the biggest threats facing modern software. The September 2025 NPM breach drove this point home by compromising libraries that sit at the core of nearly every JavaScript project. Instead of targeting small utilities, attackers went after packages like chalk and debug, dependencies woven into countless apps, frameworks, and cloud systems.
What made the incident even more alarming was its reach beyond enterprise code. To grasp its impact, we need to see how the attack unfolded, what damage it caused, and what lessons must now guide the future.
Background and Timeline of Events
On September 8, 2025, at 13:16 UTC, the first public alert came from Charles Guillemet, CTO of Ledger. He warned that a large-scale NPM compromise was underway. The root cause wasn’t a technical exploit but a phishing campaign. Attackers registered npmjs.help, a lookalike domain created on September 5. They sent emails warning that accounts would be locked unless users enabled mandatory two-factor authentication.
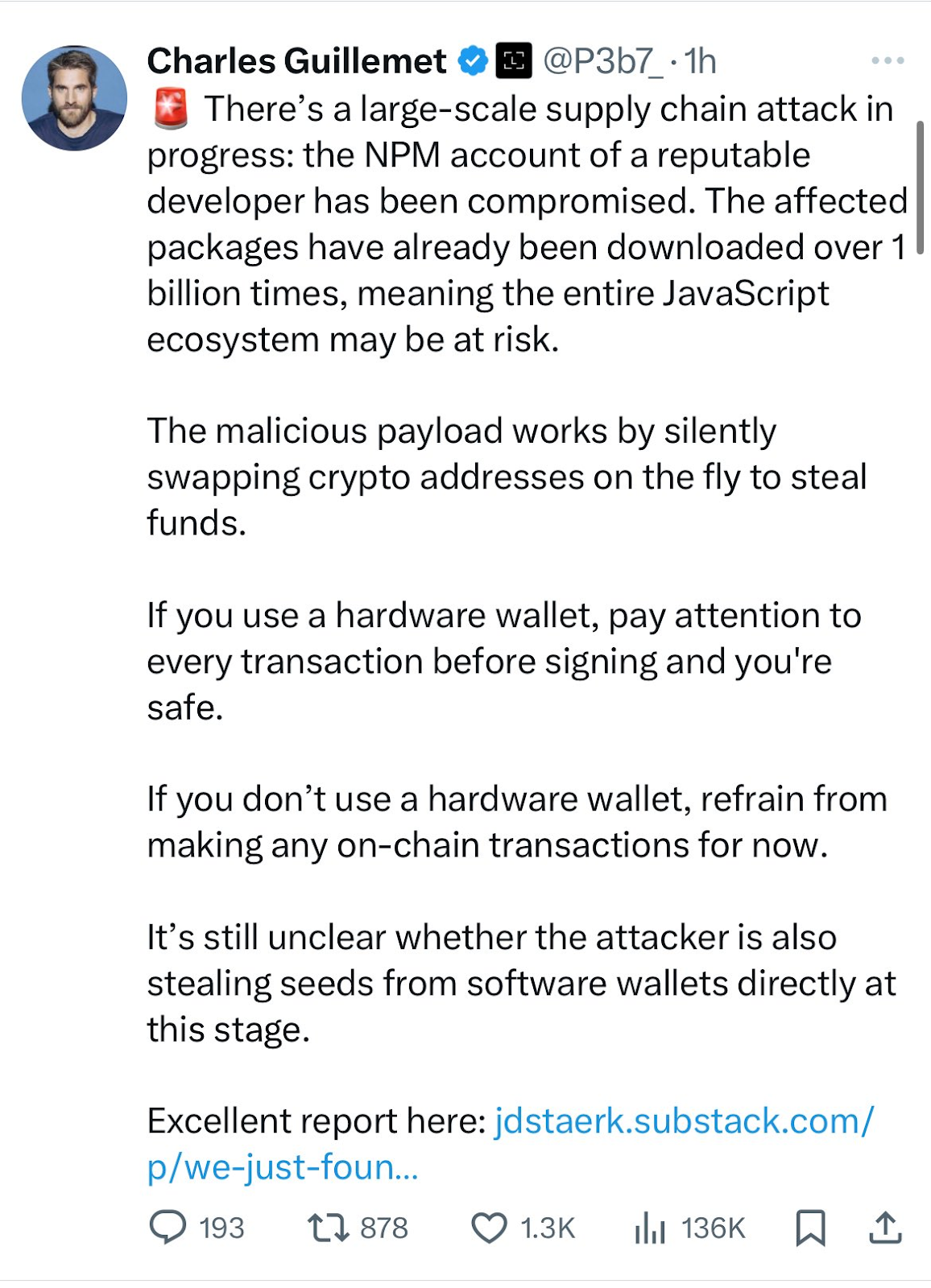
Attackers registered the domain npmjs.help on September 5. Days later, they began sending messages that looked official, warning maintainers that accounts would be locked if they did not enable mandatory two-factor authentication. For developers accustomed to fast security updates, the email carried the right mix of urgency and authority. Maintainer Josh Junon, known as “qix,” who controls some of the ecosystem’s most critical packages, was among those deceived. When he entered his credentials and time-based codes, attackers gained direct access to his NPM account.
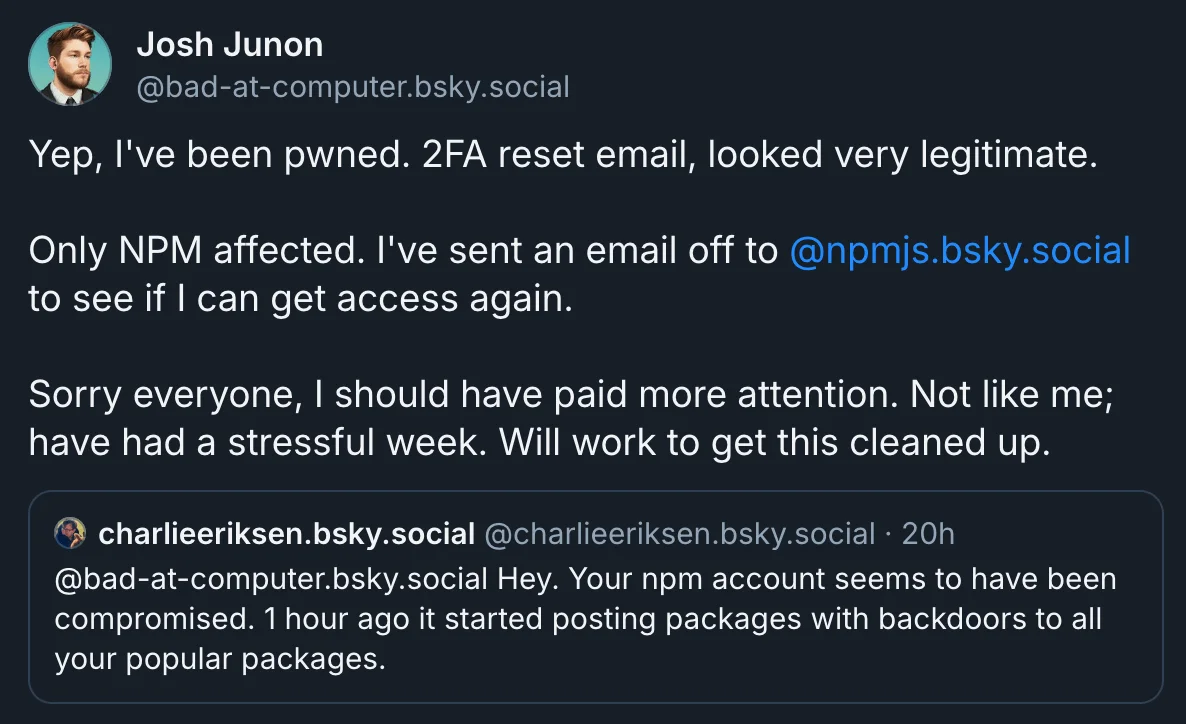
Once inside, the adversaries moved swiftly. They released new versions of chalk, a library downloaded nearly 300 million times a week, along with debug, strip-ansi, and other utilities such as ansi-styles and supports-color. These updates looked routine, nothing more than minor version bumps. But hidden inside was malicious code. Every developer who updated their project during those hours unknowingly imported the compromise, and because NPM dependencies cascade, one poisoned package rippled into countless others.
Why the Attack Was Dangerous
This breach was dangerous not simply because a few packages were altered but because of which packages were targeted. Chalk, debug, and strip-ansi are the kind of libraries that quietly power everything from developer tools to production systems. They are not glamorous, yet they are indispensable. Together, they account for more than 2.6 billion weekly downloads, meaning their reach touches nearly every modern JavaScript project in existence.
The structure of NPM amplified the problem. Dependencies layer upon one another. A developer may never install chalk directly, yet a framework they use almost certainly does. That design multiplies convenience but also multiplies risk. Automated build pipelines made matters worse. Continuous integration systems that pulled the latest versions introduced the malicious code without human review. Within hours, the attack had the potential to spread across every environment that touched those packages.
For the cryptocurrency ecosystem, the threat was even sharper. Researchers later confirmed that the malicious payload attempted to interfere with wallets and transactions. The code was designed to swap out addresses, diverting funds to attacker-controlled accounts. Even if only a fraction of Web3 users had installed the poisoned packages, the result could have been widespread theft. Unlike earlier NPM breaches that focused on mining or data theft, this attack directly targeted digital money.
Attack Mechanisms and Operations
NPM and the Dependency System
Before diving into the attack details, we need to understand what NPM is. NPM (Node Package Manager) serves as the backbone of the JavaScript ecosystem. Think of it as a massive supermarket where programmers can “shop” for the tools and libraries they need for their projects.
The special characteristic of NPM is its dependency system – the interconnected web of dependencies. When you use software package A, it might automatically pull in package B, and package B might depend on package C. This dependency chain can be very long and complex. Statistics show that modern applications average 203 dependencies, creating exponential risk multiplication where single compromised dependencies can affect all downstream consumers.
Historical Evolution of NPM Attacks
To better understand the severity of the September 2025 incident, let’s look back at the evolutionary history of NPM supply chain attacks:
The event-stream attack of 2018 marked a turning point in NPM attack history. What’s remarkable is that the attacker spent months building trust with the maintainer before injecting targeted malicious code. The attack specifically targeted the Bitcoin Copay wallet through an encrypted payload with environment-specific decryption keys, affecting 8 million downloads over 2.5 months.
The ua-parser-js incident of 2021 demonstrated sophistication in account compromise techniques. Attackers flooded maintainer Faisal Salman’s email to mask suspicious activity while conducting phishing operations, ultimately deploying coinminers and password stealers to 7+ million weekly downloads within just four hours. Notably, this incident connected to dark web forums offering developer account access for $20,000.
The colors/faker sabotage of January 2022 revealed an entirely different motivation. Maintainer Marak Squires deliberately sabotaged his own packages (colors.js with 20+ million weekly downloads, faker.js with 2.8+ million) out of frustration with corporate usage without compensation. This exposed the sustainability crisis underlying open-source maintenance.
Specific Attack Scenario for September 2025
In this incident, attackers compromised developer Josh Junon’s (@qix) account and released malicious versions of many critical software packages. The compromised packages included some of JavaScript’s most foundational libraries:
- chalk with 299 million weekly downloads
- debug with 357 million weekly downloads
- strip-ansi with 261 million weekly downloads
- color-convert, ansi-styles, supports-color and several other packages
In total, the combined impact exceeded 2.6 billion weekly downloads. Research from Wiz Security found that 99% of cloud environments contained at least one targeted package, and 10% were compromised within the two-hour window of the attack. These are all fundamental “ingredients” that thousands of other projects use.
Let’s visualize how the spreading process works: A Web3 project might not directly use these infected packages, but it depends on another library, and that library depends on one of the infected packages. When updating dependencies, malicious code silently infiltrates the system.
Impact on the Cryptocurrency World
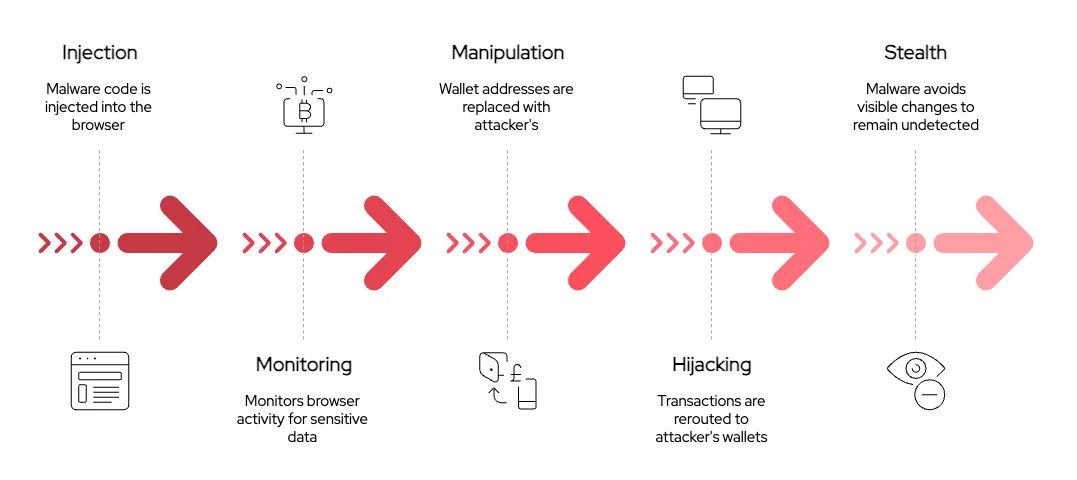
The “Clipboard Hijacker” Mechanism
The malicious code implanted in these NPM packages operates as a sophisticated “clipboard hijacker.” It has two main operating modes, each designed to deceive users in ways that are difficult to detect.
Passive mode uses the Levenshtein distance algorithm to create fake wallet addresses that look very similar to real ones. For example, if your real address is “0x1234567890abcdef”, the malicious code might replace it with “0x1234567890abcdee” – differing by only one character at the end. To the naked eye, it’s very difficult to spot this difference.
Active mode is even more dangerous. It can detect cryptocurrency wallets in browsers and directly intervene in the transaction process, changing the destination address right before the user signs the transaction.
Damage Assessment and Attacker Profits
The paradox of the September attack is that while the reach was massive, the direct financial damage was minimal. On-chain records show that the attackers stole only about $503 worth of assets. Roughly $429 came from Ethereum, $46 from Solana, and the remainder from minor tokens. For an event that touched billions of downloads, the sum looked almost trivial.
Yet the small number masks the reality of what was at stake. The limited theft was not because the attackers held back but because the community reacted fast. Within two hours, the compromise was flagged publicly. Developers began reverting to safe versions, NPM removed the malicious releases, and security researchers traced the wallets tied to the attack. The narrow window of exposure stopped the worst-case scenario before it could unfold.
The hidden costs, however, were steep. Thousands of teams paused development to audit dependencies, rebuild pipelines, and verify deployments. Business operations slowed. Trust, the invisible glue of open source, was eroded. The idea that one phishing email could compromise packages downloaded billions of times shook both developers and enterprises. Even with little financial loss, the event forced organizations to reconsider how much of their infrastructure rests on the shoulders of individual maintainers.
Community Response
Once the scale became clear, the response was swift. Alerts spread across GitHub, X, and developer forums. NPM maintainers unpublished the compromised versions and replaced them with clean releases. Security vendors such as Wiz and Sonatype confirmed that nearly every major cloud environment contained at least one affected package, evidence of how deeply embedded these libraries were.
Wallet providers also moved to reassure users. Ledger emphasized that hardware wallets remained secure because transactions must be confirmed on-device. Even if malicious code altered the address inside a browser or application, the final screen on the hardware device displayed the true recipient, creating a last line of defense. That safeguard helped prevent a modest incident from becoming a catastrophe.
The broader developer community also began shifting practices. More teams adopted Software Bills of Materials to track dependencies. Lockfiles were tightened, and CI/CD pipelines gained additional security checks. The attack was a wake-up call: supply chain trust could no longer be assumed. It had to be verified at every step.
Prevention and Protection Measures
Assessing Actual Risk Levels
Despite sounding scary, the actual impact of this incident wasn’t as severe as initially feared. This is because the attack only affected websites that had pushed updates since the hacked NPM packages were released. Other projects continued using old, safe versions.
Moreover, most experienced projects have dependency pinning procedures, meaning even when they update, they continue using previously tested, safe code.
Perspectives from Cybersecurity Experts
Major cybersecurity companies have elevated NPM supply chain attacks to the highest threat status. CrowdStrike’s 2021 Global Security Attitude Survey found 84% of organizations believe NPM supply chain attacks will become one of the biggest cyber threats. However, only 36% had vetted all vendors for security in the past year.
Mandiant describes supply chain attacks as “sophisticated attacks that abuse existing trust,” making them particularly difficult to prevent and detect. CTO Steve Ledzian emphasizes their potential for disproportionate impact, exposing multiple victims simultaneously through single compromise points.
Ilkka Turunen from Sonatype Field CTO connects NPM attacks to advanced persistent threat groups like Lazarus, noting that “package takeover is now a standard tactic” because they allow access to “a large portion of the world’s developer population by compromising a single under-resourced project.”
Cryptocurrency Wallet Defense Measures
MetaMask and the LavaMoat System: MetaMask is developing LavaMoat, a comprehensive security system providing “three-point protection” throughout the software development lifecycle. This system deploys multiple security layers including version locking, automated testing, manual review processes, and Blockaid integration for real-time malicious address flagging.
MetaMask’s security architecture includes malicious contract detection supported by the Blowfish security platform, scam NFT protection, hardware wallet integration support, and transparent monthly reports on security incidents. Their transaction preview and simulation features specifically address the address-swapping attacks seen in the September 2025 incident.
Phantom Wallet and Multi-Layer Protection: Phantom Wallet has deployed advanced transaction previews with real-time warnings for malicious transactions across Solana, Ethereum, and Polygon networks. Their security measures include malicious contract detection, community-maintained blocklists of over 2,000 malicious domains, hardware wallet integration, and comprehensive security audits by Kudelski Security and Least Report.
User Recommendations
For hardware wallet users: Experts recommend continuing normal usage but carefully checking every transaction before signing. Hardware wallets provide the crucial final layer of protection by allowing users to verify destination addresses before completing transactions.
For software wallet users: The situation is more complex because it’s unclear whether attackers directly steal seed phrases. Temporary avoidance of on-chain transactions is recommended until the situation is clarified.
Lessons and Protection
The clearest lesson from September 2025 is that supply chain security is no longer a background concern. It is a frontline challenge. For developers, dependency management must change. Updating blindly is a risk few can afford. Projects now need to lock versions, use tested builds, and run audits before integrating fresh code. Tools that generate SBOMs provide visibility into every layer of a build and should become standard practice rather than an afterthought. Stronger authentication for maintainers, including hardware security keys, reduces the chance that a single compromised login can unleash global consequences.
For the crypto community, the defense is even more straightforward. Hardware wallets remain essential. By requiring physical confirmation of addresses, they render attacks that attempt to swap transaction data ineffective. Users should take time to review every transaction, even when under pressure, and delay high-value transfers during periods of known ecosystem instability. Software wallets remain useful, but without a hardware checkpoint they leave too much room for unseen manipulation.
The human factor also cannot be overlooked. This attack succeeded because of a phishing email, not because of a flaw in cryptography. Training developers to treat urgent login requests with suspicion is as important as technical safeguards. Platforms must harden their login systems, using domain protections and stronger alerts, while teams should normalize the practice of verifying suspicious requests through official channels. In the end, vigilance is as critical as technology.
Conclusion: Resilience in the Context of Persistent Vulnerabilities
The September 2025 NPM supply chain attack will stand as the largest in JavaScript history, not for the money it stole but for the vulnerabilities it revealed. Billions of downloads were placed at risk because one maintainer’s account was compromised. That reality highlights both the fragility and the resilience of the open-source ecosystem.
On one hand, it shows that too much of the modern internet depends on a small group of unpaid maintainers. On the other, it proves that when danger emerges, the community can rally, detect, and contain the threat quickly. The malicious code is gone, yet the message remains. NPM Supply chain security is not optional. It is the frontline of cybersecurity, where the integrity of the digital world will be defended. Developers must secure their dependencies, businesses must support maintainers, and users must guard their assets with verified tools.
The internet runs on shared code. Its future depends on how carefully that code is protected. The September attack is both a warning and a roadmap; proof that vigilance, collaboration, and transparency are the only way to keep trust alive in an age of constant risk.
Malicious code has now been removed from most affected packages, and the situation is under control. However, this incident serves as an important reminder of the potential risks in modern software ecosystems and the importance of maintaining constant vigilance in the digital age.