CZ Warns of North Korean Hackers as SEAL Team Exposes 60 Fake Crypto IT Workers
Binance co-founder Changpeng “CZ” Zhao is urging crypto firms to tighten security after the white hat SEAL team uncovered 60 fake IT worker profiles linked to North Korea, highlighting a sharp rise in infiltration attempts across the industry.
- Hackers pose as job candidates, employers, or users to deploy malware and steal data.
- CZ warns crypto companies to screen candidates and train employees against phishing tactics.
- Coinbase introduces stricter security rules, including in-person training and fingerprinting.
- North Korean hackers stole $1.34B in crypto in 2024, up 102% from 2023.
North Korean hackers are escalating their efforts to breach cryptocurrency firms by impersonating IT professionals, according to a warning issued by Binance co-founder Changpeng “CZ” Zhao. In a post on X, CZ detailed how hackers pose as job candidates to gain insider access, often targeting roles in development, security, and finance. Some impersonators present themselves as employers, sending malicious links during fake interviews, while others bait employees with infected “sample code,” pose as customers to deliver harmful attachments, or even attempt outright bribery for sensitive data. CZ urged crypto platforms to rigorously vet job applicants and train staff to avoid downloading unauthorized files.
The alert coincides with a major discovery by the Security Alliance (SEAL), a white hat hacker collective led by Paradigm researcher Samczsun, which revealed a repository of at least 60 North Korean agents using fake identities to infiltrate crypto exchanges and drain user data. The database includes aliases, fake citizenships, email addresses, GitHub profiles, and salary details of the impersonators. SEAL has conducted more than 900 hack-related investigations since its 2024 launch and continues to counter sophisticated intrusion tactics.
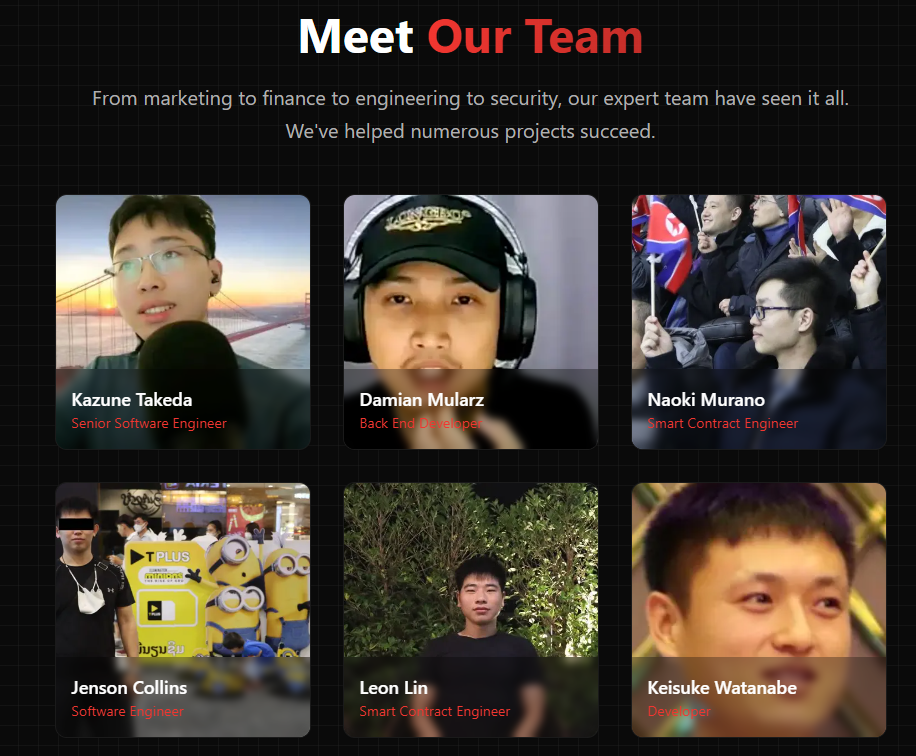
Other major exchanges are tightening security in response to these threats. Coinbase CEO Brian Armstrong announced mandatory in-person security training for employees in the U.S., as well as fingerprinting for those with system access, and new protocols to prevent phishing and malware attacks. Armstrong likened the scaleSEAL team repository of 60 North Korean IT worker impersonators. Source: lazarus.group/team of North Korea’s hacker workforce to an “endless supply line,” with hundreds of new operatives emerging every quarter.
The risks are far from theoretical. In June 2024, four North Korean operatives infiltrated multiple crypto firms as freelance developers, stealing nearly $900,000. According to Chainalysis, North Korean-linked groups like the infamous Lazarus Group stole over $1.34 billion in digital assets across 47 incidents in 2024, more than double the $660 million stolen the year before. High-profile heists, including the record-setting $1.4 billion Bybit hack, underscore how persistent and effective these attackers have become.
Final Thought
The SEAL team’s revelations and CZ’s warning show that North Korean cybercrime is a mounting threat to the crypto ecosystem. As attackers refine their tactics—using fake resumes, malicious links, and insider bribes—exchanges and blockchain firms must invest in aggressive vetting, employee education, and continuous monitoring to safeguard their platforms and users from sophisticated state-sponsored exploits.



