Risks of Smart Contracts: Bugs, Hacks, and Limitations
Key Takeaways
- Smart Contracts transformed agreements by delivering automation, transparency, and independence from intermediaries.
- Risks remain constant, with bugs, hacks, and design limits shaping how secure and reliable these systems are.
- Major incidents like the DAO hack, Poly Network, and Ronin Bridge highlight the stakes involved when vulnerabilities are exposed.
- Defenses keep evolving, from audits and bug bounties to formal verification, governance tools, and decentralized insurance.
- The future of Smart Contract security lies in smarter auditing, stronger oracle systems, standardized frameworks, and regulatory clarity.
Introduction:
Smart Contracts stand as one of the most powerful achievements of blockchain. They bring automation, clarity, and independence from middlemen. What once required lawyers, banks, or brokers can now be executed by code alone.
The reality, though, is that Smart Contracts are unforgiving. Once released on-chain, they follow instructions to the letter. We are talking about whether a hidden bug can erase millions in an instant or a loophole discovered by hackers can lead to irreversible losses. There is no reset, no second chance.
This makes Smart Contracts both groundbreaking and perilous. They are the backbone of DeFi, NFT marketplaces, and DAOs. Yet they have also fueled billion-dollar thefts, chain splits, and heated disputes about security.
In this article we will uncover the risks that come with Smart Contracts. We will examine coding flaws, sophisticated attacks, and the deeper limitations that code alone cannot solve. Real examples will show why these risks persist and how the industry is fighting to keep the promise of Smart Contracts alive.
The Promise of Smart Contracts
To see why the risks matter, you first need to understand what makes Smart Contracts so powerful. At their core, they turn agreements into self-executing code. Instead of waiting for signatures or approvals, actions happen the moment conditions are met.
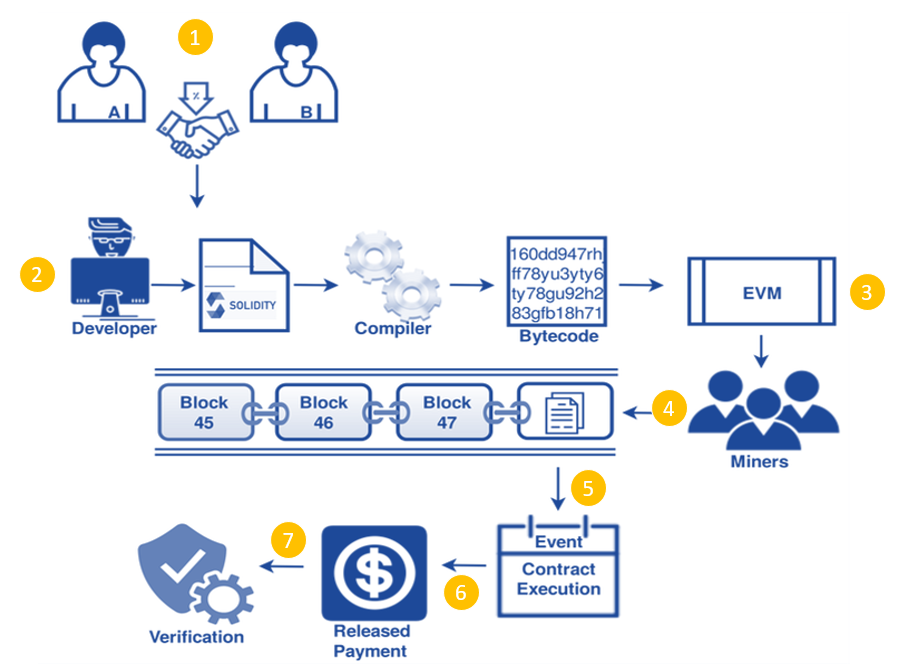
Its speed comes hand in hand with transparency. Every line of code behind Smart Contracts sits on the blockchain, open for anyone to inspect. Users do not need to trust hidden terms or private negotiations; the logic is visible, and the rules are clear. Trust moves from institutions to the code itself.
This openness also creates flexibility. Because Smart Contracts are programmable, they can be designed to handle loans, power decentralized exchanges, issue NFTs, or coordinate global communities through DAOs. They are not limited to one function. They serve as building blocks for a new digital economy.
The promise feels almost limitless. A loan can move without a bank. Proof of ownership can exist without a notary. Entire communities can organize without a central authority. With Smart Contracts, ideas that once seemed impossible now run live on-chain.
Yet the very features that give Smart Contracts their strength also introduce new weaknesses. Transparency invites not just verification but also exploitation. Immutability ensures stability, but it also means a single mistake cannot be corrected. Flexibility allows creativity, but it also opens the door to complex vulnerabilities.
And this is where the discussion turns. To truly grasp the future of Smart Contracts, one must understand their risks. Bugs, hacks, and limitations are not rare exceptions; they are recurring challenges that shape how this technology evolves.
Bugs in Smart Contracts
The saying “code is law” captures both the promise and the danger of Smart Contracts. Once a contract is deployed, it executes exactly as written. There are no revisions, no appeals, and no room for interpretation. That precision is powerful, but it also means that even the smallest bug can trigger massive consequences.
When a tiny flaw breaks everything
A single mistake in logic can cause funds to freeze, balances to reset, or contracts to behave in ways the developers never intended. Unlike traditional software, you cannot simply push an update to fix the issue. On the blockchain, the bug becomes permanent unless drastic action is taken, such as deploying a new contract or even forking the network.
Common coding errors in Smart Contracts
Some of the most damaging vulnerabilities have been surprisingly simple:
- Reentrancy loops: A contract allows repeated calls before its state is updated. Attackers exploit this to drain funds repeatedly in a single transaction.
- Integer overflows and underflows: A calculation goes beyond its expected limits, resetting balances or producing negative values.
- Access control flaws: Functions that should be restricted end up exposed, giving outsiders unintended power.
- Uninitialized variables: Developers forget to set defaults, creating loopholes in the contract’s logic.
- Gas limit mismanagement: Transactions that exceed gas limits stall execution and can lock funds indefinitely.
The DAO hack: a turning point
The DAO hack in 2016 remains the defining example. The DAO was designed as a decentralized venture fund, raising over 150,000 ETH, worth about 60 million dollars at the time. It promised token holders a chance to vote on projects and shape the future of decentralized governance. But its contract carried a reentrancy flaw. Attackers spotted it and repeatedly called the withdrawal function before the system updated balances, draining funds step by step. Within days, a massive portion of the DAO’s assets had been siphoned away. The aftermath split Ethereum into two chains, one that reversed the theft and one that preserved the original ledger. That schism created Ethereum and Ethereum Classic, leaving the blockchain world with lasting debates about immutability and governance
Even today, despite years of research and thousands of audits, bugs in Smart Contracts continue to cause billion-dollar losses. The complexity of decentralized applications makes human error almost inevitable. Every new feature or upgrade adds fresh risk, and because these contracts manage real value, attackers are highly motivated to find even the smallest oversight.
The result is a paradox. Smart Contracts promise mathematical certainty, yet their safety often depends on fallible human developers. Which is why, after bugs, we must turn to an even darker threat: deliberate attacks.
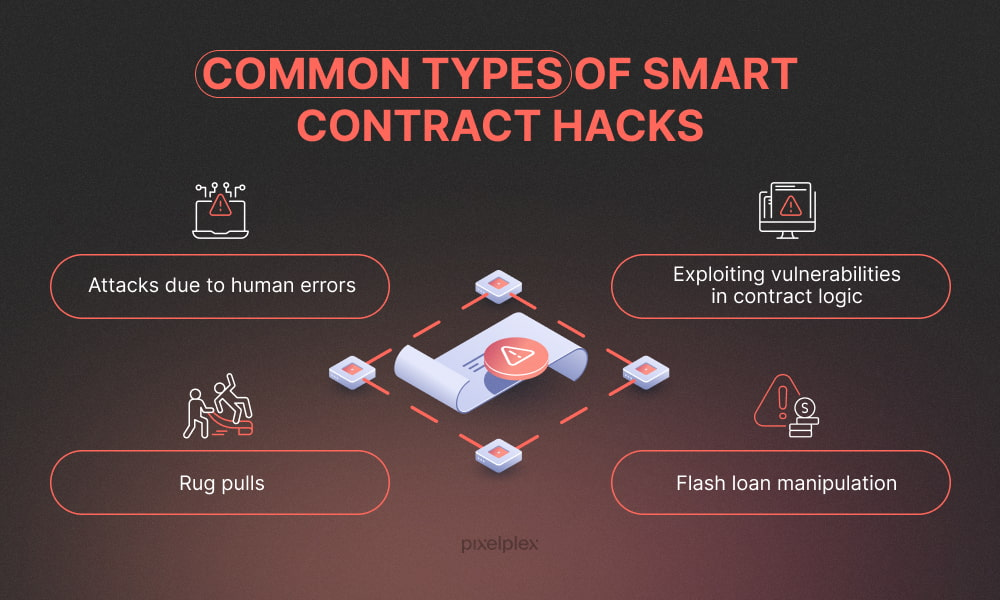
Hacks Exploiting Smart Contracts
Bugs expose flaws unintentionally, while hacks weaponize them. Because Smart Contracts are fully transparent on the blockchain, attackers can examine every line of code as closely as auditors. What was designed to inspire trust also offers adversaries a clear view of potential weaknesses.
The incentives are enormous. DeFi channels billions of dollars each day, and Smart Contracts hold these assets directly. Once an exploit is activated, value shifts instantly according to the instructions embedded in code. The system executes faithfully, even when that execution benefits an attacker.
Heists that shaped the industry
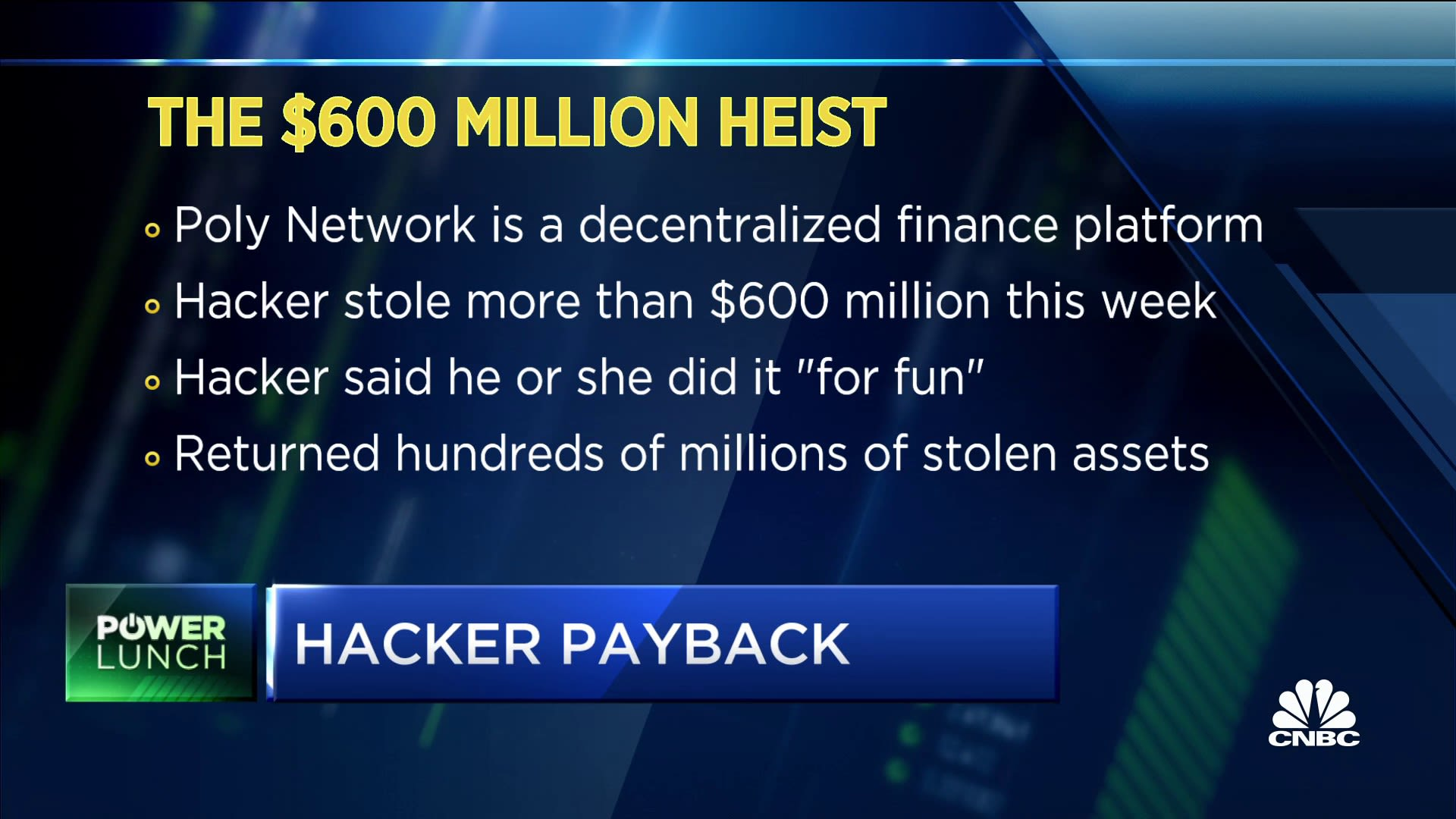
In 2021, Poly Network’s cross-chain contracts were manipulated to redirect more than 600 million dollars. The attacker later returned the funds, but the breach revealed how fragile complex cross-chain logic could be.
The following year, Ronin Bridge suffered an even larger loss. By seizing validator keys linked to its Smart Contracts, hackers drained 620 million dollars from the network that powered Axie Infinity. Millions of players felt the consequences, and the attack marked a turning point in how the industry viewed bridge security.
Soon after, Wormhole lost 320 million because its contract failed to validate signatures. Not long after, Nomad collapsed into chaos when a faulty update allowed anyone to replicate transactions and withdraw funds. Hundreds of wallets joined the frenzy, stripping away 190 million dollars in just a few hours. These events underscored how a single weakness can escalate into a systemic crisis.
The attacker’s playbook
Despite different targets, the methods often echo each other. Flash loans provide instant liquidity that fuels aggressive market manipulation. Oracles supply essential data yet become vulnerable when the information flow is corrupted. Bots lurking in the mempool jump ahead of profitable transactions, taking advantage of predictable order flows. And in some cases, the greatest risk comes from within. Developers embed hidden functions, drain liquidity, and disappear, leaving behind what the community calls a rug pull.
Why the cycle persists
Every exploit demonstrates the same reality: Smart Contracts execute instructions exactly as written. When attackers discover a path to profit, the blockchain delivers results without hesitation.
Security audits strengthen defenses, but the pace of DeFi innovation keeps creating unfamiliar scenarios. Teams push new products to market quickly, and each launch introduces fresh complexity. Meanwhile, attackers work with patience and precision, testing every edge.
This creates a repeating cycle. A breach reveals vulnerabilities, the industry adapts with stronger safeguards, and new innovations open fresh possibilities for exploitation. Smart Contracts continue to evolve, and so do the threats that surround them.
Beyond intentional attacks lies another dimension of risk, the structural limits that come from the very design of Smart Contracts. Understanding those limits is essential for seeing both the potential and the boundaries of this technology.
Limitations of Smart Contracts
Even when Smart Contracts run flawlessly and avoid attacks, they still face built-in boundaries. These limits are not bugs or oversights but natural consequences of how the technology works. They shape what contracts can achieve today and define the challenges ahead.
| Limitation | Explanation | Impact |
| Immutability is also a constraint | Smart Contracts stay fixed once deployed, which makes flaws or outdated terms cannot be adjusted. | – Adaptability suffers, creating friction for developers and users.- Need new deployments or complex governance to correct mistakes. |
| Dependence on oracles | Contracts depend on external oracles for real-world data. | • Wrong or manipulated data still triggers execution• Reliability tied to oracle integrity |
| Legal and regulatory gaps | Smart Contracts function as code, but legal systems struggle to interpret them. | • Disputes remain unresolved• Weak enforcement across jurisdictions |
| Usability and accessibility | Writing and using contracts requires technical skills and tools. | • Adoption limited to tech-savvy groups• User experience still complex |
| Scalability pressures | Heavy use clogs networks, raising fees and slowing performance. | • Congestion during demand peaks• Users face high fees and delays |
Understanding these limitations is just as important as recognizing the risks of bugs and hacks. Only by acknowledging the full picture can the industry create Smart Contracts that are both effective and sustainable.
Mitigation Strategies
The risks surrounding Smart Contracts are serious, yet the industry has developed an expanding set of defenses. Developers, auditors, and entire communities contribute to a security culture that makes contracts more resilient. Each measure strengthens the system, raising the cost of attacks and building user trust.
Security audits
Audits form the first barrier. Independent specialists review contract code before it goes live, identifying vulnerabilities that internal teams may have missed. They highlight weak points, propose fixes, and stress-test the design against known exploit methods. A contract that passes a rigorous audit stands on much firmer ground.
Formal verification
For systems holding enormous value, some teams choose formal verification. This method applies mathematics to prove that the contract logic behaves as intended in every scenario. The process is demanding and expensive, yet it delivers a higher level of certainty. Projects such as MakerDAO rely on this assurance for their core protocols.
Bug bounties
White-hat hackers play a key role in prevention. Platforms like Immunefi run bounty programs that pay researchers for responsibly reporting flaws. The incentives encourage security experts to compete with attackers, often finding issues before they can be exploited. To date, these programs have paid out millions and saved far more.
Upgrade mechanisms and governance
Some developers build upgrade paths into their Smart Contracts. Proxy patterns make it possible to replace contract logic while preserving user balances. Governance layers such as multi-signature approvals and timelocks add oversight, ensuring that upgrades happen transparently and with community involvement. This combination balances stability with adaptability.
Risk pooling and insurance
Decentralized insurance has begun to emerge as a final layer of protection. Platforms like Nexus Mutual allow users to purchase coverage against Smart Contract failures. In the event of an exploit, policyholders can recover part of their losses, reducing the impact of catastrophic events. Insurance introduces a safety net that reassures participants in high-risk environments.
Each defense reflects a hard lesson from past crises. The DAO collapsed elevated audits. Bridge failures highlighted the need for formal verification and robust oracles. Rug pulls pushed communities toward stronger governance. Every shock reshaped the landscape and drove the industry toward better practices.
Mitigation does not guarantee perfection, yet it creates resilience. With overlapping defenses in place, Smart Contracts become harder to exploit and innovation gains room to grow with greater confidence.
The security journey, however, does not end here. As Smart Contracts expand into more industries and carry larger value, the tools protecting them must evolve just as quickly.
The Future of Smart Contract Security
Smart Contracts will continue to grow in scale and influence. As DeFi expands, NFTs evolve, and enterprises adopt blockchain, the value locked in these systems will reach levels that rival traditional finance. With that growth, security must advance at the same pace—or faster.
Smarter auditing tools
Manual audits remain essential, yet they cannot keep up with the sheer volume of new contracts. The next wave will combine human expertise with automated tools powered by machine learning. These systems will scan for patterns across thousands of deployments, flagging risks that even experienced auditors might overlook.
Standardized libraries and frameworks
Most vulnerabilities arise from reinventing the wheel. By relying on standardized, battle-tested libraries, developers can reduce the chance of introducing critical flaws. Just as traditional software matured around common frameworks, Smart Contracts will increasingly depend on shared building blocks vetted by years of use.
Stronger oracle designs
Oracles remain a weak point, but new models promise more resilience. Decentralized oracle networks, cryptographic proofs, and cross-checking data sources all aim to reduce the chance of manipulation. As contracts become more interconnected with the real world, reliable data feeds will define their credibility.
Regulation and compliance
Governments are moving closer to shaping how Smart Contracts operate. Some jurisdictions may soon require audits or security certifications before contracts manage public funds. While regulation brings challenges, it could also standardize protections and force higher quality across the industry.
Insurance and risk markets
Financial safeguards will expand alongside technical ones. Insurance protocols are still young, yet they point toward a future where risk can be priced, traded, and distributed. If Smart Contracts are to rival banks and payment systems, users will expect the same sense of coverage against failure.
A moving frontier
The trajectory of Smart Contract security is clear. Attacks will not vanish, but defenses will keep rising. Each breakthrough in exploitation drives an equal breakthrough in protection. The systems that endure will be those that treat security not as an afterthought but as an evolving discipline, woven into every stage of design and deployment.
In short, Smart Contracts will always carry risks, but the future belongs to the teams and communities that transform those risks into resilience.
FAQs
Are Smart Contracts safe?
They are secure when written and audited properly, but no Smart Contract is risk-free. Bugs, hacks, and oracle manipulation have all led to major losses, so caution is always necessary.
Can Smart Contracts be changed after deployment?
Most Smart Contracts are immutable once deployed. Some use upgradeable designs with proxy patterns, but changes usually require governance approval and strict safeguards.
What is the biggest risk with Smart Contracts?
Exploits targeting vulnerabilities remain the biggest danger. High-profile cases like the DAO or Ronin Bridge show that even well-funded projects can suffer massive losses from a single flaw.
How do users protect themselves?
Choosing audited protocols, avoiding untested projects, and using DeFi insurance when available all reduce exposure. Staying informed about known risks is also essential.
Conclusion: Balancing Power and Risk
Smart Contracts have redefined how agreements are made and enforced. They remove middlemen, deliver automation, and enable entire industries from DeFi to NFTs. Their promise is undeniable, but the path has never been without obstacles.
Bugs, hacks, and built-in limits have cost billions and forced communities to face hard choices. Each incident, from the DAO to Ronin Bridge, showed that Smart Contracts are only as strong as their code and the systems around them. Yet each crisis also fueled progress, inspiring better audits, stronger governance, and new security practices.
The future will demand even greater discipline. As Smart Contracts carry more value and touch more industries, their safety will depend on constant innovation in both technology and governance. They are not flawless, but with awareness, careful design, and evolving safeguards, Smart Contracts can remain one of the most powerful tools of the digital age.



